Blog
Data Safe Group LLC »
Check out our blogs to stay up to date with the latest trends in the IT world and insights on keeping your company’s data safe and secure.
Introducing Data Safe SaaS Defense
Fortify critical business data with a multi-layered application that secures, protects, and defends against malicious attacks that target Microsoft 365. Data Safe Group is excited to announce an advanced threat protection for Microsoft 365 users. With our improved...
How to Implement a Cyber Resilience Strategy
The most common definition of cyber resilience is the ability of an enterprise to limit the impact of security incidents. It’s a broad approach that encompasses cybersecurity and business continuity management, which aims to defend against cyber attacks andensure that...
The Importance of Cyber Resilience
Did you know that 60% of businesses that suffer a cyber attack go out of business within six months? The vast majority of damage is due to the inability of the company to respond because they have not developed a cyber prevention and response strategy. If your...
Why Accountants Choose File Protection
Data Safe's File Protection is a secure and scalable file and folder backup service that is designed to efficiently protect accounting and finance companies and recover data across devices such as workstations, laptops, and file servers. Without access to a simple,...
How to Secure Your Home Office
When establishing a safe environment at home, we put locks on the doors, latches on the gate, and home security systems that keep uninvited visitors out, and alert us to any intruders otherwise. What we see is what we address – as is the case with most things and...
Why Does My Business Need SaaS Protection Software?
Great SaaS Protection ensures that we, as managed IT service providers, can access, control, and most importantly protect their your business whether using Microsoft 365 and/or Google Workspace data. [video width="640" height="360"...
How MSPs Can Prevent, Detect, and Respond to Ransomware Attacks
Ransomware attacks have all but dominated news headlines in recent weeks. Managed service providers (MSPs like us) know the risks of ransomware and how important it is to have a plan in place to respond to an attack when they have an impacted client. There are many...
What is Cyber Resilience?
Becoming cyber resilient is not an overnight endeavor. Security and resilience have been in Data Safe Group's culture from the start. We can help guide your cyber resilience journey. What is Cyber Resilience? Cyber Resilience is a measure of business strength in...
How to Prevent Ransomware: An Increasing Threat
Ransomware is nothing new. The first recorded example was in the late 1980s and it continues to spread at an accelerated pace. Did you know ransomware attacks are anticipated to cause $20 billion in damage this year, which is 57 times higher than in 20151? No business...
How Your Business Can Recover Quickly from Any Disaster
To ensure you are protected, get beyond these myths and misconceptions about Business Continuity and Disaster Recovery Making Sure Your Business Is Ready for Anything You’ve seen disasters in the news that could be fatal to your business. They range from unforeseen...
Should Your Company Outsource IT? Key factors to help you decide what’s best for your company.
IT service providers deliver the technical expertise small businesses need at a much lower cost than hiring IT staff. They can recommend, install, and manage technology according to business’ objectives and core competencies and ensure that critical data is safe....
How to Start Building Cyber Resilience with Tools You Already Use
You may have heard the term “cyber resilience” around the IT channel as of late but may not know what it is, much less how to get started with it. A close cousin to cybersecurity, cyber resilience takes the “get a good lock on your doors” approach several steps...
The Aftermath of a Ransomware Attack: Downtime Hurts, BCDR Helps
There has been no shortage of ransomware attacks in the news lately with major targets like Bose, Electronic Arts, and Colonial Pipeline Co. The small and medium businesses (SMBs) of the world know all too well that ransomware is about more than just getting your data...
The Top Five Industries Targeted with Ransomware
Ransomware has been on the rise for years, but 2020 and 2021 have ushered in a new level of threat and frequency as criminals shift their focus from large enterprises to small-medium businesses (SMBs). At Data Safe Group, we are seeing the dreaded ransomware scenario...
What is Immutable Cloud Storage?
Utilizing the cloud for backup has become fundamental to business continuity and disaster recovery (BCDR) best practices. Small business owners are realizing that not all solutions that employ the cloud are the same, however. There are significant differences in cloud...
Why SaaS Protection for Microsoft 365?
Have you moved critical data from on-premises apps to cloud-based apps such as Microsoft 365? Are you doing all you can to keep it safe? SaaS applications don’t provide the deeper layers of protection you need. We explain how they fall short in our eBook DOWNLOAD –...
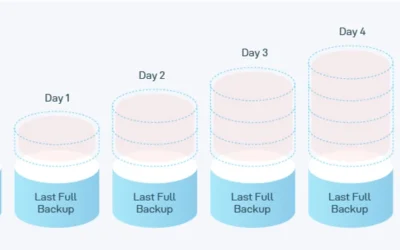
Incremental vs Differential Backup – What is the Difference?
The main difference between incremental and differential backups is how they save space and time by storing only changed files. However, the effectiveness of incremental backups is very different from differential backups. Before we dive into the differences between...
SaaS Protection Initiatives
Every day thousands of organizations, just like yours, place their trust in Microsoft 365 to safeguard business-critical data including vital emails, customer data, and sensitive documents. But did you know data stored in Microsoft 365 is just as vulnerable to...
What is Ryuk Ransomware and How Does it Work?
Ryuk is a type of ransomware that once deployed encrypts files on an infected system. Ransom is typically demanded in bitcoin or other types of cryptocurrency. Ryuk has targeted many large organizations using Microsoft Windows and related systems. First spotted in...
When Is It Time To Update Your Software?
>It’s that little alert on your desktop. The “upgrades available” indicator when you check your computer. Or when your smartphone tells you that it’s going to update later while you’re sleeping, and you defer it to another time. What if you miss an email or a text?...
Why Are We Normalizing Breaches?
Back in August of 2019, Facebook was the victim of a data breach that compromised information from 533 million people from 106 different countries. Why is this news now? Because the breach was addressed in a recent email from Facebook management, and that email was...